blog
Greymatter and Cybersecurity Mesh Architecture: Support at the Security Analytics and Intelligence Layer
How Greymatter enables the Cybersecurity Mesh Architecture Security Analytics and Intelligence Layer.

July 13, 2023
By the Greymatter Technology, Innovation, and Outreach Team
In a prior blog, we explained how Greymatter.io and the strengths of the Greymatter Application Networking Platform make us ideally suited to support several key tenets of Gartner’s Cybersecurity Mesh Architecture (CSMA)1, which consists of four essential layers working together: security analytics and intelligence, identity fabric, centralized policy and posture management, and operations dashboard. Here, we’re going to focus on how Greymatter supports the security analytics and intelligence layer with near real-time collection and delivery of contextualized threat data.
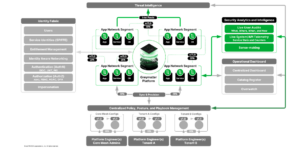
Figure 1: CSMA and Greymatter
Why now
Currently, organizations use multiple tool sets for security analytics, correlation, and threat detection, including their SIEM, XDR solutions, SOAR platforms, and UEBA2, as well as IDP/IPS, NTA, and vulnerability scanning tools. The effectiveness of these tools depends on the data they receive. However, configuring systems to pipe data into these tools and curating that data for ingestion and analysis requires significant work by development and engineering teams. And SOC analysts spend time building queries to extract the data they need, iterating with engineers and developers on adjustments before finally arriving at a set of normalized, relevant, and actionable data.
The challenge compounds as organizations move to hybrid environments consisting of multiple cloud instances, multiple instantiations within a single cloud, and on-prem feature sets. Manual processes and increasing complexity make it costly to keep up and difficult to provide detailed real-time data on the disparate instances supporting the business operations. Teams struggle to gain the security intelligence they need to understand what’s happening across their environment and protect their operations.
Organizations need a more efficient and effective way to strengthen their security posture and mitigate risk of breaches at scale. The CSMA security analytics and intelligence layer is designed to address this need, as it encourages an integrated, relationship-based approach for monitoring and analyzing network traffic to detect and prevent security threats.
Why Greymatter
Greymatter plays a crucial role in enabling the security analytics and intelligence layer so that clients can address compliance, operational uptime, and security requirements more quickly and easily. Here are just a few top uses cases.
Automation and analytics out-of-the-box
Getting auditing information, especially on applications and APIs, with user fidelity at the enterprise level is expensive. Typically, infrastructure logs just show the path of traffic, which often isn’t sufficient to address compliance requirements. Obtaining details like live user tracking to see paths by users and the data they touched, requires a significant amount of custom audit code and is expensive to write on your own. In fact, some organizations have told us they spend millions of dollars and hundreds of hours of developer and engineering time tooling for auditing. Greymatter does this out-of-the box and provides continuous streams of actionable data.
Deep visibility into endpoint, API, and application traffic in real-time
Organizations struggle to stay ahead of anomalous activity and potential threats and take proactive measures to protect their assets and avoid disruption of service. For example, when DDoS attacks happen, such as the recent attack on a popular gaming site3, service can be disrupted for hours or days. With live user tracking and the ability to see the health of a system – including a surge in traffic on a particular endpoint, API or application in real time – Greymatter is able to drop anomalous traffic and automatically redirect good traffic to an API or application in a different region to protect the user experience.
Enhanced insights and root cause analysis
Government agencies and large enterprises with mission critical operations need to be able to collect user and telemetry data for attribution, forensic analysis, and analysis on important missions and customers. Greymatter integrates seamlessly with security tools such as SIEM, SOAR, and XDR from vendors including Splunk and Elastic Search to enrich analysis with user and network data. Organizations can gain a more complete picture of potential threats and attacks from a cybersecurity perspective to help mitigate risk and accelerate resolution.
How Greymatter does it
Greymatter inherently facilitates CSMA’s security analytics and intelligence layer through scorecard heuristics and risk contextualization in combination with SIEMs, SOARs, and other tools mentioned earlier. Specifically:
- Greymatter integrates with and streams data into these tools in the form of live user audits that consist of who is doing what, when, where, and how, to enable comprehensive and improve the accuracy of security threat detection systems.
- Beyond the usual statistical network information, live system/API telemetry and our unique approach to identity enables us to understand how people, systems, and processes are behaving compared to what they are authorized to do.
- This deep visibility into application networking traffic and transactions based on enhanced data, which can be correlated with other information collected, further enriches network traffic analysis.
- Our sense-making models allow security teams to use this information to monitor and analyze application behavior, detect anomalies and potential threats, and understand network traffic patterns.
Other complementary capabilities include integration with threat intelligence systems, real-time updates on the latest application networking traffic and identity attribution, as well as network and user pattern of life analysis audits that allow security teams to identify and track potential threats based on user and network behavior over time. Overall, Greymatter provides a comprehensive suite of capabilities that support the security analytics and intelligence layer across an enterprise.
What’s in it for our clients
Just as clients benefit from Greymatter.io’s head start in Zero Trust, our clients can also gain meaningful value from our early support for CSMA’s security analytics and intelligence layer, including:
- Cost savings by significantly reducing the resources required to write high-fidelity, custom audit code.
- Improve threat detection capability accuracy, speed response, and provide real-time analytics with deep visibility into traffic and behaviors for analysis and action, including on-the-fly traffic rerouting to avoid disruption.
- Improved incident resolution with the ability to overlay telemetry data with automatic failover measures to maintain availability, and then seamlessly send data to security tool sets for analysis and resolution.
As we continue to build our operational view of what is happening on the network and provide those insights to clients, Greymatter users can expect to see even more connectivity and analysis capabilities at the security intelligence and analytics layer, including advancing our unique sense-making models to conduct security health checks at the service level and treat problems to mitigate risk.
In our next blog, we’ll specifically address how Greymatter connects and contributes to CSMA’s identity fabric layer.
Contact us today to schedule your free consultation, determine your microservices maturity level, and build a reference implementation architecture to begin moving your organization up the microservices maturity model to accelerate software delivery and increase speed to market, while ensuring security.
Further reading:
1https://www.gartner.com/en/doc/756665-cybersecurity-mesh
2https://www.code42.com/blog/gartner-renames-ueba-category-to-insider-risk-management-solutions/
3https://gamerant.com/blizzard-ddos-attack-battlenet-april-2023/

