blog
Greymatter and Cybersecurity Mesh Architecture: Support at the Identity Fabric Layer
How Greymatter enables the Cybersecurity Mesh Architecture Identity Fabric Layer.

July 22, 2023
By the Greymatter Technology, Innovation, and Outreach Team
In a prior blog, we explained how GreyMatter supports the security analytics and intelligence layer of Gartner’s Cybersecurity Mesh Architecture (CSMA)1. Here, we’re going to focus on our support of the identity fabric layer, arguably the most important layer of CSMA because it serves as the backbone, providing a unified and integrated approach to identity and access management (IAM).
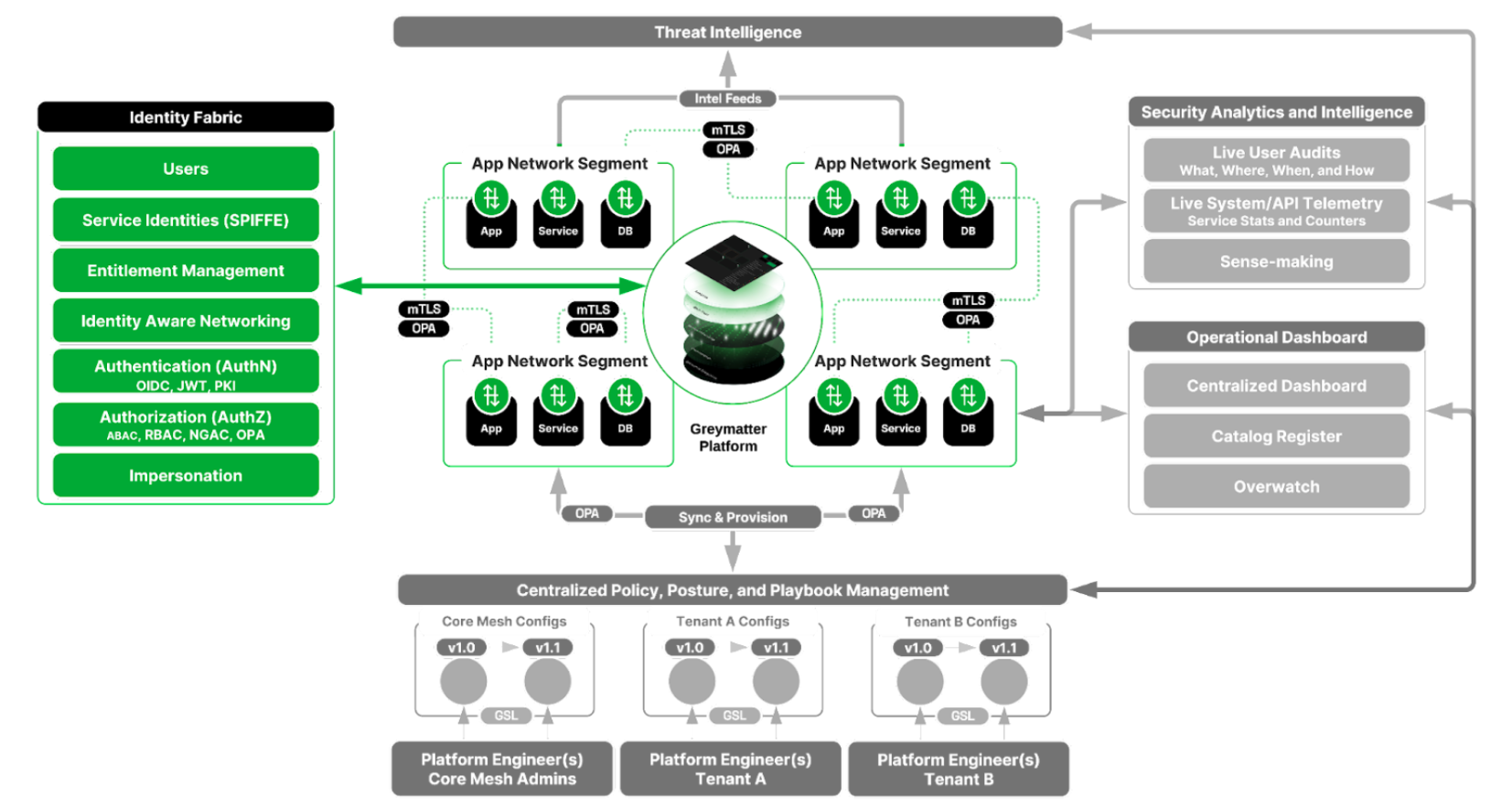
Figure 1: CSMA and Greymatter
Why now
Managing user and system identities and access in today’s hybrid, multi-cloud environments is incredibly complex. Organizations often have IAM solutions from multiple, external identity providers to manage different types of identities, applications, and access requirements. This results in siloed and fragmented identity management environments, which can lead to inefficiencies, security risks, and compliance issues.
Furthermore, applications often leverage different authentication and authorization mechanisms, leading to gaps in identity awareness. Auditing capabilities also differ depending on the code or application, making it difficult to maintain a complete picture of user identity across the network. And while OIDC is widely adopted, token exchange abilities are limited, forcing organizations to pass around large user claims to all network assets, regardless of need. Widespread propagation of identity and associated attributes allows threat actors to see what that user has access to, which opens the lens to an attack vector.
The CSMA identity fabric layer is designed to address growing complexity and eliminate silos by encouraging a centralized approach to identity and access management, while still enabling the ability to segment identity based on network location, application, service, or network asset.
Why Greymatter
Greymatter plays a unifying role in the identity fabric layer, delivering a comprehensive and consistent view of identities, access controls, and policies across the environment. Clients can improve security, simplify compliance, and streamline IAM operations. Here are a few top use cases.
Secure service-to-service communication
Organizations struggle to secure their microservices-based architecture and ensure that only authorized services are communicating to each other. Implementing and managing service-to-service communications for every transaction, in compliance with their security policies and industry regulations, is incredibly complex and time-consuming. And the challenge mounts as new services and capabilities are introduced. Greymatter eliminates the complexity and improves security by providing service-to-service identity attestation, certification rotation, and policy enforcement out-of-the-box to help prevent unauthorized access to sensitive data and transactions.
Identity management across hybrid and multi-cloud environments
Today, 87% of organizations have a multi-cloud strategy2, and each cloud environment has its own IAM solution. What’s more, many organizations continue to operate on-premises infrastructure. Not every IAM solution is created equally, which creates a management challenge as teams move between different IAM solutions with different views of identities, access controls, and policies. With support for OIDC compliant interfaces, Greymatter eliminates the need to manage separate IAM solutions and provides a unified view of identities and access controls across multiple clouds and hybrid environments.
Identity and claims segmentation
In highly regulated industries such as healthcare or financial services, balancing employee access to applications and services with compliance policies and regulations such HIPAA, GDPR, and PCI can be difficult. By using Greymatter’s identity and claims segmentation capabilities, institutions can strike that balance, ensuring that only the necessary identity attributes and access controls are provided to each application and service, based on employee role and location, reducing the risk of exposure. Additionally, all interactions are logged and stored providing transparency and auditing capabilities.
Role-based and fine-grained access control
The move to a Zero Trust framework often entails looking into adopting a role-based access control (RBAC) and attribute-based access control (ABAC) model. Adding yet another layer of tools to their tech stack to manage isn’t something most teams are eager to do. To simplify adoption of RBAC and ABAC, clients can leverage Greymatter’s support of open policy agent (OPA) to define RBAC and ABAC policies for fine-grained access control, customized based on the organization’s requirements.
Centralized identity infrastructure
In an effort to unify their IAM environment, organizations increasingly choose an IAM product that supports OIDC integration. However, they soon discover that most of their applications need to be updated to support the OIDC specification, which requires significant coding and developer time. This unplanned expense slows widespread adoption throughout the enterprise and pulls developers away from more strategic initiatives. Greymatter streamlines the process with built-in support for OIDC authentication and authorization capabilities, so integration is fast and easy.
How Greymatter does it
As an application networking platform, Greymatter inherently supports CSMA’s identity fabric layer with a range of capabilities that enable organizations to manage identities and access controls centrally across hybrid and multi-cloud environments, while decentralizing and simplifying enforcement. Specifically:
- To validate user identity, organizations use various authentication mechanisms, whether PKI, MFA, OIDC, JWT tokens, or something else. With built-in support for OIDC, Greymatter provides a centralized way to bring together different authentication methods and tools to simplify authentication so that it flows seamlessly through the network based on the user and the service, application, or data they need to access.
- Within Greymatter, each service also receives its own identity. Greymatter’s SPIFFE/SPIRE integration enables automated and secure issuance and revocation of identity certificates for services. Control over service identities helps to prevent unauthorized access to sensitive data and transactions within the microservices environment.
- Leveraging an organization’s need to ensure least-privilege access policy models, policy layer, Greymatter taps into the role-based access control (RBAC), attribute-based access control (ABAC), and next-generation access control (NGAC) based approaches that the security teams develop using Open Policy Agent (OPA) Rego. This helps offload the work for development teams. Every service that is tied into the Greymatter application networking platform can benefit from the organization’s centralized policy engine and fine-grained access controls.
- We further strengthen security by rotating service identities on an hourly or configurable basis. In the event of a service compromise, entitlement management reduces the blast radius and mitigates risk as threat actors must regain access to the service and organizations have a greater opportunity to detect a compromise.
- The ability to understand both user and system identities and claims and propagate that information across hybrid and multi-cloud environments in a seamless and automated fashion enables identity aware networking. Greymatter unifies identities across external identity providers such as Keycloak, Okta, Google, and Microsoft and provides only the necessary identity attributes and access controls specific to each application, service, or network asset, based on the employee’s role and location.
- We make it easy for organizations to leverage Open Policy Agent (OPA) to write and configure RBAC and ABAC authorization policies for each service at a granular level via a centralized, repeatable process. Integration with Greymatter ensures that only authorized users have access to specific resources, for example applications, APIs, and sensitive data. Access can be automatically blocked based on contextual data such as request payloads, device posture, location, and more.
- Greymatter supports impersonation for additional security, whereby authorization to access a service is dependent on their having already accessed another service. Access controls are defined so that if a user tries to access that service directly then access is denied. Linking the user and service together provides additional fine-grained controls and is easy to configure as part of Greymatter’s role-based access control configurations.
Additional capabilities include scalability and high availability features, logging of all authentication and authorization activity, comprehensive reporting and auditing, and integration with security tool sets. Overall, Greymatter offers a comprehensive and battle-tested suite of capabilities that support the identity fabric layer today, and as organizations scale and expand their IT environments.
What’s in it for our clients
Our clients gain meaningful value from our early support for CSMA’s identity fabric layer, including:
- Improved threat detection, response, and real-time analysis by eliminating silos and gaining real-time capabilities and granular visibility into who’s doing what, where, when, and how for analysis and action.
- Improved incident resolution with detailed logs of all interactions between users, services, applications, data, and assets, and exporting of data to security tool sets for analysis and resolution.
- Increased regulatory compliance with fine-grained controls to maintain strict compliance with regulations such as NIST 800-207 and 800-207A publications, GDPR, HIPAA, and PCI, as well as capabilities that increase transparency and audit-ability.
Cost savings by streamlining operations – including reducing the number of IAM solutions in place and development time – and reducing the cost of a breach.
As we continue to build out our federated identity, fine-grained access control, and identity aware networking functionality, organizations can expect to see an even broader view of their identity landscape that will further simplify the management of user and service identities, access control policies, and network security. An even more efficient, effective, and dynamic identity management system will provide a seamless user experience to the infrastructure team, enabling them to focus on other critical tasks.
In our next blog, we’ll specifically address how Greymatter connects and contributes to CSMA’s centralized policy, posture, and playbook management layer.
Contact us today to schedule your free consultation, determine your microservices maturity level, and build a reference implementation architecture to begin moving your organization up the microservices maturity model to accelerate software delivery and increase speed to market, while ensuring security.
Further reading:

