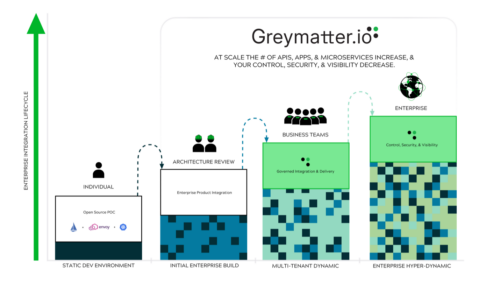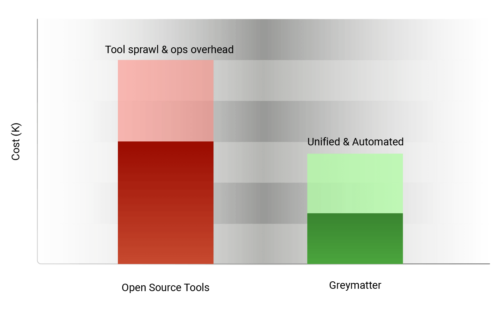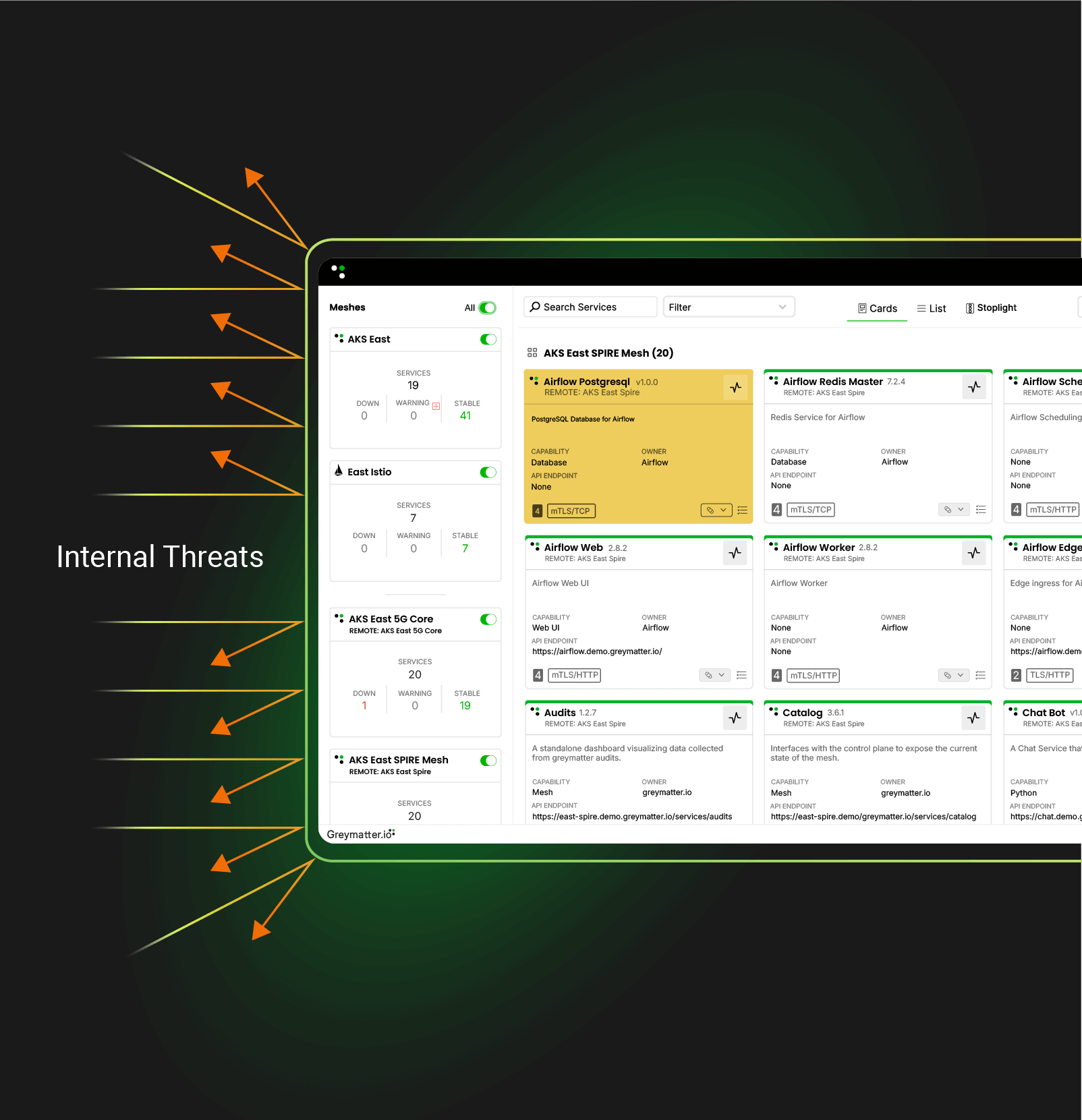
The Path to Zero Trust Modernization
Eliminate Implicit Trust. Secure Every Interaction.
Perimeter defenses no longer work. Attackers now exploit trust gaps between services, clouds, and legacy systems.
Your security model should protect you—not expose you.
Traditional Security is Failing
Attackers Don’t Just Break In—They Log In
Implicit trust allows unauthorized users and services to move laterally across networks. Without zero trust, every connection is a potential breach.
Zero Trust is Too Complex to Deploy
Most enterprises lack the expertise and resources to implement zero trust across distributed workloads, microservices, and hybrid environments.
API & Service Communication is Unprotected
Service-to-service communication is the most targeted attack surface. Greymatter blocks lateral movement with granular policy enforcement.
Lack of Visibility into Access and Activity
Security teams struggle with blind spots across cloud, on-prem, and edge workloads, leaving them unable to enforce consistent policies.
Compliance is Costly and Hard to Maintain
Organizations in regulated industries must comply with FIPS, NIST Zero Trust, DoD Impact Levels, ISO 27001, SOC 2, GDPR, and more, but achieving and maintaining compliance is time consuming and resource intensive.
Zero trust eliminates these risks—but only if implemented correctly.
That’s where Greymatter comes in.
A step-by-step approach to eliminating risks
The Six Phases of Zero Trust Security
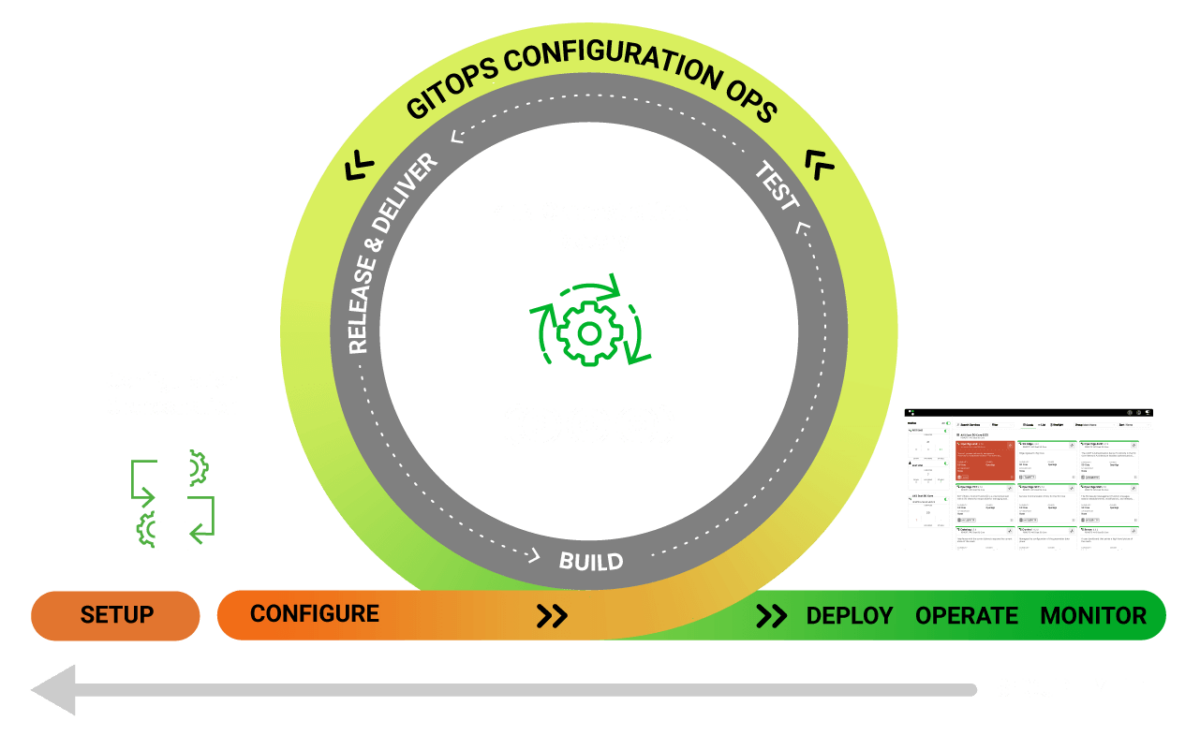
Zero trust isn’t a single tool—it’s a transformation. Greymatter ensures workloads meet or exceed foundational cybersecurity controls—from audit logging to boundary protection to least privilege enforcement.
Phase 1: Assess & Strategize
How Greymatter Delivers:
- Prioritize high-risk access points and align to zero trust controls.
- Enforce military grade zero trust with FIPS encryption for all connections.
- Create versioned GitOps playbooks to define desired security state and enforce it automatically.
Phase 2: Identity & Access Modernization
How Greymatter Delivers:
- Enforce strong authentication across cloud, hybrid, and legacy workloads without code changes.
- Authenticate and authorize every request with granular policy enforcement points before access is granted.
- Apply Role-Based & Attribute-Based Access Control (RBAC/ABAC) and least-privilege access for users, workloads, and APIs.
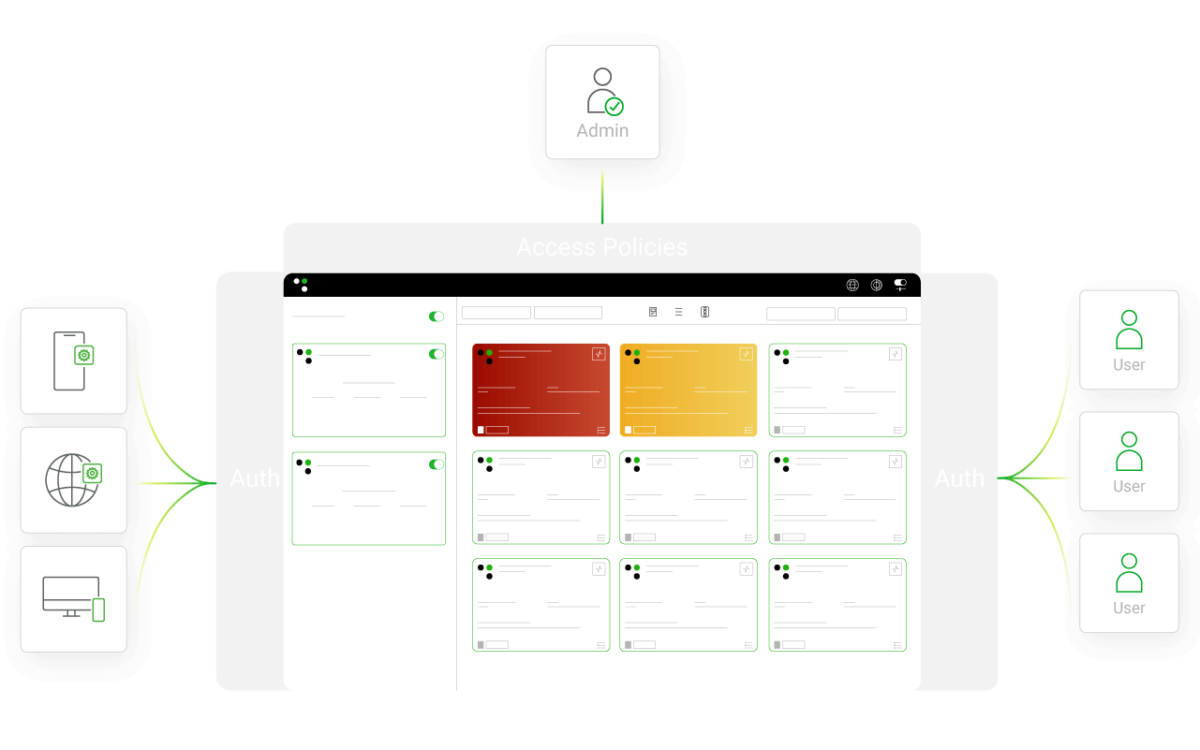
Phase 3: Enforce Network Segmentation & Policies
How Greymatter Delivers:
- Limit access between workloads, reducing the attack surface.
- Dynamically grant or deny network access based on granular security policies and workload identities.
- Adjust and enforce security policies based on orchestrated policy managed via GitOps playbooks.
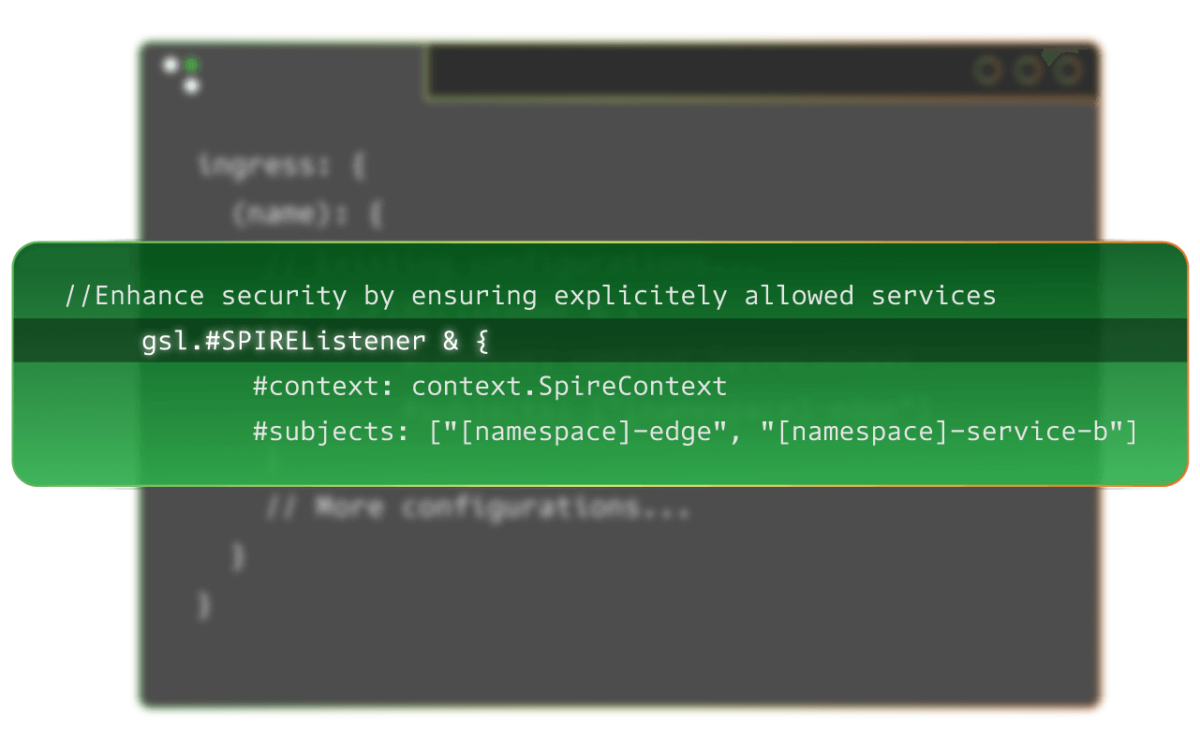
Phase 4: Secure Service-to-Service Communication
How Greymatter Delivers:
- Encrypt and upscale service-to-service communications to the latest protocol standards and ciphers to prevent eavesdropping and tampering.
- Assign unique cryptographic identity, ensuring only verified workloads interact.
- Manage dynamic NPE Certificates automatically issues, rotates, and revokes certificates without manual intervention.
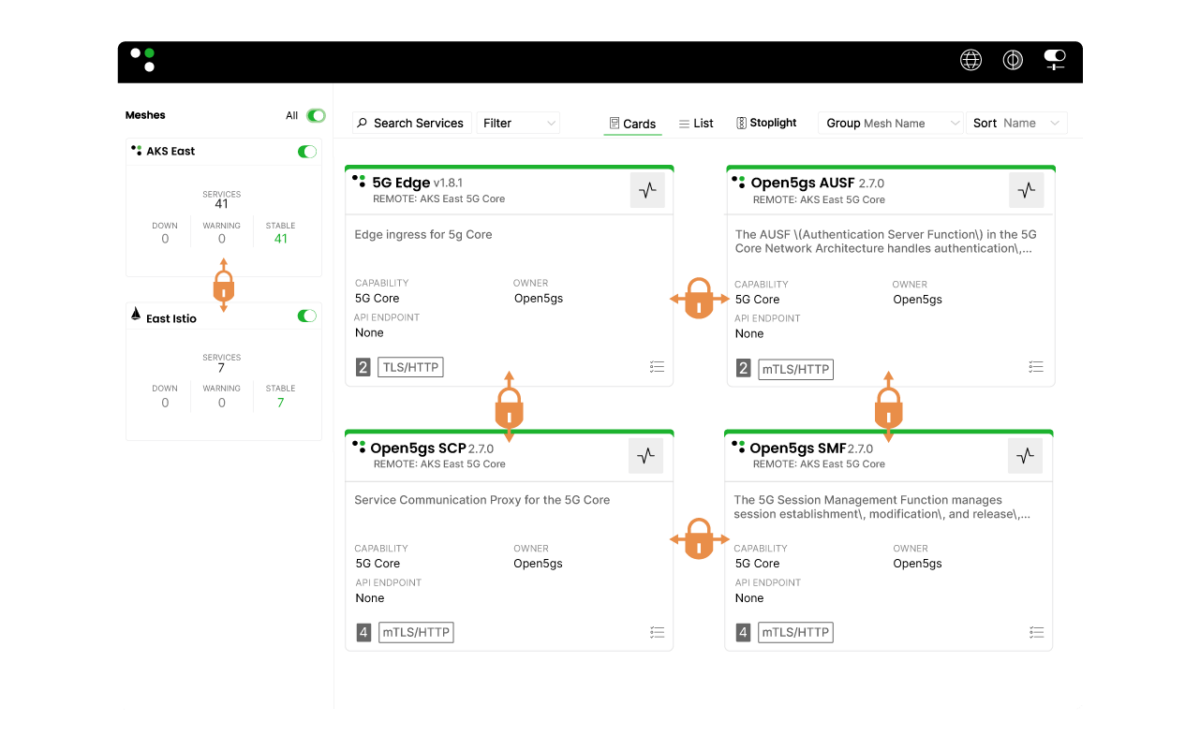
Phase 5: Continuous Monitoring & Access Control
How Greymatter Delivers:
- Monitor network traffic, API calls, user actions, and workload interactions.
- Apply policies for changing conditions with a single save, stopping threats before they escalate.
- Send logs, traces, and access records to tools like Grafana, Prometheus, and Splunk for security analysis and compliance.
Phase 6: Governance & Compliance Automation
How Greymatter Delivers:
- Ensure security policies align with NIST Zero Trust, DoD Impact Levels, and FedRAMP requirements.
- Provide forensic level visibility into security events for compliance reporting.
- Maintain an immutable audit trail of all playbook changes via Git.
Case Study: DoD Zero Trust 2.0, Operationalized
Built to Align with the Mission—
Not Just the Mandate
Greymatter doesn’t just check the boxes. It enforces zero trust across all DoD pillars using automation and policy control—ready for DoD Impact Levels, SCIF, and multi-domain operations.
DoD Zero Trust Pillar
How Greymatter.io Delivers
User
Enforces MFA, SSO, and RBAC/ABAC.
Integrates with PKI and oAUTH for user access models.
Device
Controls access using mTLS-bound workload identities and explicit networking orchestration rule sets. Denies all by default unless explicitly permitted.
Application & Workload
Issues cryptographic identities for each workload.
Applies zero trust policy enforcement at service-to-service level and on all ingress gateways.
Data
Encrypts all traffic in transit (mTLS). Enforces least-privilege data access through policy and tagging.
Network & Environment
Segments traffic via micro-mesh deployments. Uses policy-bound routing, gateways, and multi-mesh mTLS enforcement.
Visibility & Analytics
Streams instant telemetry to SIEM/SOAR platforms. Logs access decisions, policy outcomes, and forensic traces.
Automation & Orchestration
Uses GitOps and declarative playbooks for networking orchestration and granular security policies, deployment, and rollback.
Policy & Governance
Aligns with DoD / NIST Zero Trust, DoD Risk Management Framework, FIPS encryption, DoD IL2-IL6+, and FISMA. Enforces all policies via code and validates compliance via audit trails.
Breaches Aren’t Waiting.
Why Should You?
Every second your organization delays zero trust, the attack surface grows. Greymatter delivers the automatic security and compliance you need—without complexity.