A Hands-On Guide for Developers Managing Multi-Mesh Environments
Managing multiple service meshes across clusters, regions, or clouds introduces significant operational complexity for platform and DevOps teams. Greymatter Mesh Connections eliminates these challenges with end-to-end automation, zero trust security, and instant observability—enabling encrypted, policy-aware inter-mesh connectivity and failover, all orchestrated through declarative GitOps workflows.
When two or more Greymatter and Istio meshes connect, they follow a secure, automated handshake to ensure only trusted parties communicate:
- Both Catalog A and Bridge Edge B start by loading their own security certificates and keys. Each also loads the other’s certificate for trust.
- Bridge Edge B loads a whitelist to control which catalogs are allowed to connect.
- Catalog A opens a connection to Bridge Edge B. Bridge Edge B checks Catalog A’s certificate for authenticity.
- Bridge Edge B sends its own certificate back, and Catalog A verifies it.
- Once both sides trust each other, Catalog A requests the mesh configuration.
- Bridge Edge B double-checks Catalog A against the whitelist, gathers the needed mesh data, and sends the configuration back.
This process ensures that only authorized catalogs can connect, and all communication is encrypted and verified. See Figure 1 below for the handshake sequence.
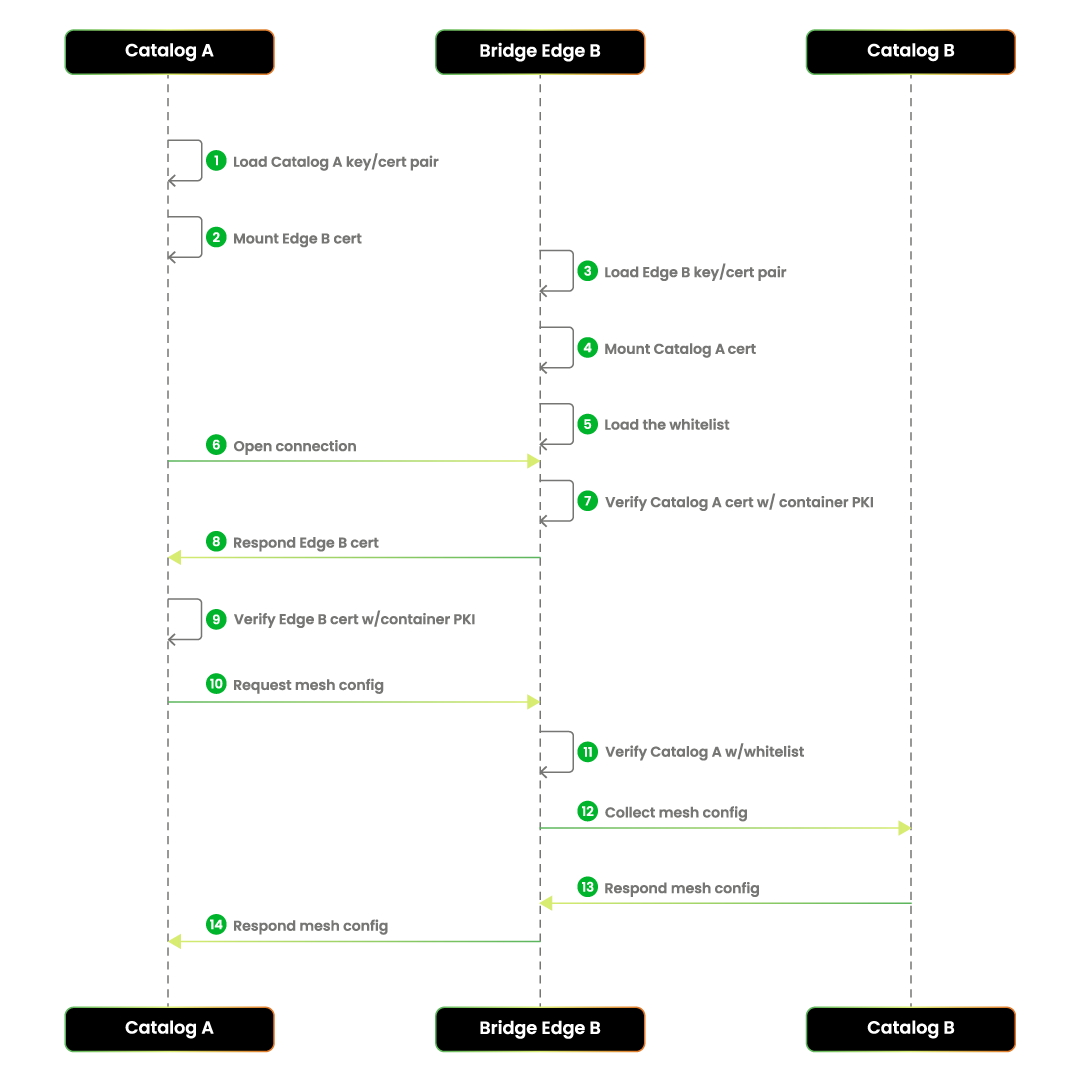
Figure 1
This guide provides a practical, step-by-step approach to enabling Mesh Connections, setting up multi-cloud failover, and synchronizing services from a centralized repository, empowering you to deliver resilient, compliant, and scalable architectures.
Why Mesh Connections with Greymatter?
- Unified Multicloud Connectivity: Seamlessly connect services across AWS, Azure, GCP, on-prem, and sovereign clouds—no brittle integrations, just one platform.
- Workload-Centric Zero Trust: Enforce NIST Zero Trust and FIPS compliance automatically, with mTLS at every hop and workload identity baked in.
- Instant Observability: Gain forensic-level audits, real-time telemetry, and automatic compliance checks—no blind spots, no manual tuning.
- Automated GitOps Workflows: Prevent configuration drift and accelerate deployments with declarative, version-controlled policies.
Step 1: Set Up Your Certificates
Establish public mTLS between meshes for secure, zero trust communication across clusters.
Recommendation: Use CA-signed certificates for production.
Step 2: Enable Incoming Connections on Mesh B
In Mesh B’s config.cue, enable mesh connections and define secure inbound sockets:
defaults: {
mesh_connections_enabled: true
}
#AcceptConnections
#Connections & {
inbound_socket: {
tls: #InboundTLSConfig
}
}This configuration allows Mesh A services to securely discover and interact with Mesh B services, enforcing policy and encryption at every layer.
Step 3: Configure Outgoing Connections on Mesh A
In Mesh A’s config.cue, define the outbound connection:
defaults: {
mesh_connections_enabled: true
}
#Connections & {
connections: {
"mesh-b": {
mesh_catalog_api: "https://mesh-b-catalog.example.com:10710"
greymatter_public_url: "https://mesh-b.example.com"
tls: #OutboundTLSConfig & {
ssl_config: {
sni: "mesh-b.example.com"
verify_certificate_spki:[<fingerprint>]
verify_certificate_hash:[<fingerprint>]
}
}
}
}
}Step 4: Deploy Bridge Services for Traffic Failover
Deploy a bridge.yaml to each mesh to enable north-south traffic and failover capabilities.
- Expose an ingress listener (default 10908 or 9443)
- Define upstreams and listeners with #HealthCheckFilter
- Configure impersonation proxies to route traffic to backup services
You can configure Greymatter to impersonate a backend service from another mesh and reroute traffic when the primary backend fails.
Example route config:
routes: {
"/backend": {
upstream: #Upstream & {
name: "bridge",
namespace: context.globals.namespace
},
health_check: {
timeout_ms: 1000,
interval_ms: 2000,
unhealthy_threshold: 2,
healthy_threshold: 5,
http: {
path: "/health"
}
}
}
}Greymatter can impersonate backend services from another mesh, automatically rerouting traffic if the primary backend fails—enabling seamless, policy-driven failover.
Step 5: Centralize Policy via GitOps
Use a shared Git repository to manage configuration for multiple meshes.
- Commit to a common branch (e.g., main or multi-cloud-sync)
- Let greymatter pull and apply changes
- Validate it is working through Sense UI, Lens, or command line
Greymatter supports:
- Blue/Green deployments with weighted traffic
- Namespace segmentation
- Shared tagging of services (e.g., east, west, prod, test)
Pro Tip: Greymatter’s declarative state management prevents drift and accelerates compliance audits.
Real Example: Multicloud, Multi-Region Deployment
A platform team deployed an application across Azure AKS and AWS EKS, managed by a central Git repository with GSL-based policy and configuration. They gradually shifted traffic from 50/50 to 100% green. When the ASK mesh failed, traffic seamlessly failed over to the EKS mesh.
Metrics achieved:
- 99% reduction in implementation time compared to manual configurations
- 60% lower total cost of ownership versus open source alternatives
- 95-99% reduction in outages
- NIST compliance alignment completed in under a month
Each deployment:
- Verified commit hash and branch consistency
- Completed autonomous provisioning of all necessary application networking tooling
- Passed health checks in the Sense UI
Security Considerations
- All mesh connections enforce NIST/DoD Zero Trust with mTLS and workload identity.
- RBAC and policy orchestration are managed centrally and applied automatically across all meshes.
- Every connection, route, and policy is auditable and version-controlled.
Already Built Into Greymatter
Greymatter Mesh Connections includes:
- Automatic Mesh Discovery and Registration
- Multi-Region Failover Routing
- Cross-Mesh Policy Orchestration
- Dynamic Topology View in Sense
Greymatter keeps Mesh B read-only from Mesh A to preserve ownership while providing full visibility and control for routing and policies.
Next Steps
Mesh Connections empowers your platform team to manage services securely and automatically across cloud, region, and network boundaries—without reinventing your workflows.
